Try SDXL Turbo For Free!
Enter your prompt and wait for a second, let SDXL Turbo amaze you.

The night I became a superhero. College aged super bodybuilder. Massive Muscles. Awesome powers. Frat house common room. Night. Photorealistic.

When we got our powers. 2 teen super bodybuilders. Massive Muscles. Awesome powers. Locker room. Night. Photorealistic.

Wide-angle shot of a creative budget backyard featuring a comfortable and stylish seating area made entirely from repurposed wooden pallets. The pallets should be arranged to form a sofa and a coffee table, complete with comfortable cushions and throws in various textures and patterns. String lights are draped overhead, creating a warm and inviting atmosphere. Add some potted plants and a simple outdoor rug to define the space. The lighting should be soft and slightly dim, suggesting an evening setting. Show the resourcefulness and charm of DIY pallet furniture. Realistic, natural light, high detail.

A Bargello needlepoint piece featuring a pattern of interconnected diamonds. The diamonds should appear to be cascading down the fabric, with subtle variations in color within each diamond to create a sense of depth and sparkle. Consider using metallic threads in some of the diamonds to enhance the 'cascade' effect.

A poignant underwater photograph of a small, pale seahorse clinging to a piece of discarded fishing net. The background is a blurred and out-of-focus view of other pieces of plastic debris floating in the water. The lighting is slightly muted and somber, conveying a sense of urgency. The seahorse's eye is visible and seems to be looking directly at the viewer.

A close-up, macro photograph of a bright yellow dwarf seahorse clinging delicately to a strand of green seagrass. The seahorse is facing the camera with its eye clearly visible and in focus. The background is a soft, blurred bokeh of turquoise water with dappled sunlight filtering through. The lighting is warm and natural, highlighting the texture of the seahorse's skin. Use a shallow depth of field to isolate the subject.

Exterior medium wide shot of a single modern minimalist container home in a sunny, open field. The home features large glass sliding doors and windows, with a clean white exterior and subtle wood accents. The surrounding landscape is green with wildflowers. Golden hour lighting, high detail, realistic, architectural photography

We have become more than human. 2 College aged super bodybuilders. Massive Muscles. Awesome powers. Dorm room. Night. Photorealistic.

We have been chosen to become more than human. 2 College aged super bodybuilders. Massive Muscles. Awesome powers. Dark alley. Night. Photorealistic.

The night we were chosen to become superheroes. 2 teen super bodybuilders. Massive Muscles. Awesome powers. Dark alley. Night. Photorealistic.

The night we received our powers. 2 super bodybuilders. Massive Muscles. Awesome powers. Empty weight room. Night. Photorealistic.

Wide-angle shot of a cheerful budget backyard featuring a freshly painted wooden fence in a warm, inviting color (e.g., soft blue or sage green). In the foreground, showcase a set of old wooden patio furniture that has been beautifully refurbished with a fresh coat of paint or stain in complementary colors. Add some colorful throw pillows and a simple outdoor rug to complete the cozy seating area. The lighting should be bright and sunny, highlighting the transformative power of paint. Include some vibrant potted flowers nearby. Realistic, high detail.

A close-up shot of a Bargello needlepoint piece featuring the traditional flame stitch pattern. The colors should transition smoothly from deep reds and oranges at the base to bright yellows and golds at the tips, creating a realistic flame effect. The stitches should be neat and uniform, showcasing the rhythmic flow of the pattern.

An underwater photograph of a solitary seahorse swimming in open blue water. The seahorse is a light brown color and is facing away from the camera, seemingly venturing into the vastness of the ocean. The background is a gradient of deep blue, suggesting depth. The lighting is natural, with sunlight reflecting off the water's surface in the distance.

Exterior medium wide shot of a luxurious, two-story container home with a loft-style design. The home features high ceilings visible through large windows, premium materials like dark metal and rich wood, and a sophisticated architectural design. The setting could be a modern, upscale neighborhood or a scenic overlook. Elegant lighting, high detail, realistic, luxury container home architecture

We had just become superheroes. 2 College aged super bodybuilders. Massive Muscles. Awesome powers. Dark alley. Night. Photorealistic.

Close-up of a charming frog figure constructed from natural materials. The frog's body is formed by a large, slightly curved brown leaf, and its legs are made from small, thin brown twigs glued to the sides. Two smaller green leaves are used for the frog's eyes, and tiny black seeds are glued onto the green leaves as pupils. The frog is sitting on a piece of light-colored bark with a blurred background of a forest floor. Warm, natural light, high detail, handmade frogs, environmental education.

We are now brothers, bound by our superpower. 2 College aged super bodybuilders. Massive Muscles. Awesome powers. Empty weight room. Night. Photorealistic.

The night we were chosen by Zeus. 2 College aged super bodybuilders. Massive Muscles. Awesome powers. Empty weight room. Night. Photorealistic.

The night we became superheroes. College aged super bodybuilders. Massive Muscles. Awesome powers. Frat house common room. Night. Photorealistic.

A close-up portrait of a woman in her late 30s with a layered, light brown bob that falls just below her chin. The layers are soft and create a gentle, flowing effect. She has a warm smile and kind eyes, wearing a delicate floral blouse. The background is a softly blurred garden with pastel-colored flowers. Soft, natural light, photorealistic, shallow depth of field.

A young girl around the age of 12 with beautiful blue gray eyes and sparkling honey blonde hair she is freckles dotting her nose and cheeks and she is wearing an orange camp half-blood T-shirt and she's also wearing black hiking pants she has a quiver full of arrows a strapped across her back and she's holding her bow in one handA young girl around the age of 12 with beautiful blue gray eyes and sparkling honey blonde hair she is freckles dotting her nose and cheeks and she is wearing an orange can't have Blood T-shirt and she's also wearing black hiking pants she has a quiver full of arrows a strapped across her back and she's holding her bow in one hand

A super macro photograph of an incredibly tiny pygmy seahorse clinging to a vibrant purple gorgonian coral branch. The seahorse is a mottled orange and white color and is almost invisible against the coral. Its tiny snout is pointed upwards. The background is a blurred view of more colorful coral. The lighting is sharp and focused, highlighting the intricate details of both the seahorse and the coral.

Exterior medium wide shot of a rustic container home nestled in a lush forest. The home has a weathered brown exterior with natural wood siding and a pitched roof. Large windows offer views of the surrounding trees. Soft, dappled sunlight filters through the leaves. High detail, realistic, nature photography

We are now more than human. 2 College aged super bodybuilders. Massive Muscles. Awesome powers. Dorm room. Night. Photorealistic.

Overhead view of several smooth, gray river stones that have been painted to resemble frogs. Some are painted solid green with black and white eyes, while others have more intricate patterns in shades of green, brown, and yellow. One painted stone frog has a small red painted tongue. The painted stones are arranged on a light brown wooden surface with a few scattered green leaves. Natural sunlight, high detail, art projects, creative activities.

We are no longer ordinary men. 2 College aged super bodybuilders. Massive Muscles. Awesome powers. Flying through the night sky. Night. Photorealistic.

We are now supermen. 2 super bodybuilders. Massive Muscles. Awesome powers. Locker room. Night. Photorealistic.

Wide-angle shot of a magical budget backyard at dusk, beautifully illuminated with a network of warm white string lights strung across fences, trees, or a pergola (if present). Include several stylish solar-powered lanterns placed on tables, pathways, or hanging from hooks, casting soft, inviting glows. The overall ambiance should be enchanting and cozy, perfect for evening relaxation or entertaining. Show the strategic placement of lights to highlight different areas of the backyard. Realistic, low light, high detail.

A Bargello needlepoint piece that resembles a modern mosaic. The pattern should be made up of small blocks of different colors and patterns within the Bargello stitch, creating a textured and visually rich surface. The color palette could be a mix of bold and muted tones

plants are beautiful

A medium shot photograph of a male pot-bellied seahorse with a visibly swollen brood pouch. Tiny, translucent baby seahorses are just beginning to emerge from the pouch. The male is a mottled brown color and is gently holding onto a piece of seaweed with its tail. The background is a dark, out-of-focus ocean floor with some scattered pebbles. The lighting is slightly dramatic, focusing on the seahorse and its pouch.

Exterior medium wide shot of a two-story modern industrial container home in a bustling urban environment. The home has a dark grey exterior with exposed steel beams and large industrial-style windows. A rooftop terrace with modern furniture overlooks a city skyline at dusk. Dramatic lighting, high detail, realistic, architectural photography

We are now supermen. 2 College aged super bodybuilders. Massive Muscles. Awesome powers. Empty weight room. Night. Photorealistic.

Close-up shot of two charming frog figures crafted from brown pinecones. One frog is painted a bright green with large googly eyes glued on, and the other is left natural brown with small green felt circles for eyes. Both have small green pipe cleaner legs and a red felt tongue sticking out. They are sitting on a bed of green moss with a few small, colorful wildflowers scattered around. Soft, diffused lighting, high detail, handmade, DIY crafts.

We have been chosen to become supermen. 2 College aged super bodybuilders. Massive Muscles. Awesome powers. Empty weight room. Night. Photorealistic.
What is Stable Diffusion 3 and what's new in it ?
Innovative Technologies and Architecture
Released on April 17, 2024, Stable Diffusion 3 features cutting-edge technologies such as the rectified flow technique and the Multimodal Diffusion Transformer architecture. These advancements streamline the image generation process and improve the integration of visual and textual data, significantly enhancing the quality and accuracy of the generated images.
Enhanced Text and Image Quality
The model utilizes a powerful combination of text encoders, including CLIP G14, CLIP L14, and T5 XXL, which greatly improve the text rendering capabilities, particularly in terms of spelling accuracy. It is trained on diverse datasets like COCO 2014 and ImageNet, using advanced de-duplication techniques to ensure a wide variety of high-quality training examples.
Scalability and Open-Source Ethos
Demonstrating its scalability, Stable Diffusion 3 shows continuous improvement with increases in model size and data volume. Stability AI’s commitment to open-sourcing the model promotes transparency in AI development and helps reduce environmental impacts by avoiding redundant computational experiments. This approach ensures that the benefits of AI advancements are accessible to a broader community.
SDXL Turbo Examples

Key Features and Benefits of SDXL Turbo
Revolutionary Performance
SDXL Turbo sets a new standard in text-to-image generation with its groundbreaking Adversarial Diffusion Distillation (ADD) technology. This innovative approach allows for rapid, single-step image generation, a significant leap forward from the traditional multi-step processes.
Enhanced Image Quality
Unlike other models, SDXL Turbo produces images of exceptional clarity and detail. By leveraging the strengths of Generative Adversarial Networks (GANs), it ensures images are crisp and vivid, avoiding common issues like blurriness or artifacts.
Real-Time Generation Capabilities
Ideal for applications demanding speed and efficiency, SDXL Turbo excels in generating high-quality images in real-time. This makes it a perfect fit for dynamic environments such as video games, virtual reality, and instant content creation.
Computational Efficiency
On high-end GPUs like the A100, SDXL Turbo can generate a 512x512 image in just 207ms, including prompt encoding, a single denoising step, and decoding. This efficiency represents a monumental improvement in both time and energy consumption over previous models.
Wide Range of Applications
The model’s versatility makes it suitable for diverse applications, from creating artistic and design works to aiding in educational and research projects. Its real-time generation ability opens new possibilities in interactive media and online content creation.
User Accessibility
SDXL Turbo’s ease of use is a key feature. With simple setup requirements and an intuitive interface on platforms like Clipdrop, it’s accessible to both professionals and hobbyists alike, regardless of their technical background. - Research and Development Opportunities: For researchers and developers, SDXL Turbo presents an unparalleled opportunity to explore advanced AI in image synthesis. The model’s unique approach and performance offer a rich ground for academic and commercial research.
In-Depth Technical Details and Model Information of SDXL Turbo
Innovative Model Architecture
At the core of SDXL Turbo lies the novel Adversarial Diffusion Distillation (ADD) technique. This unique architecture combines the best of generative adversarial networks (GANs) with diffusion model technologies, enabling the model to synthesize high-fidelity images in just a single step. This significant technical innovation represents a leap forward from the foundational SDXL 1.0 model, making SDXL Turbo more efficient and powerful in image generation.
Comprehensive Research and Development
Developed and funded by Stability AI, SDXL Turbo is the result of extensive research and development efforts. It stands as a distilled version of the SDXL 1.0, specifically trained for real-time synthesis. The model's design and training process are detailed in an extensive research paper, which is available for public access. This document offers deep insights into the technical workings and the innovative aspects of SDXL Turbo.
Technical Specifications
SDXL Turbo excels in generating photorealistic images from text prompts in a single network evaluation. This capability is a result of the Adversarial Diffusion Distillation method, which allows for high-quality sampling in one to four steps. The model is fine-tuned from the base of SDXL 1.0, maintaining high image quality while dramatically reducing the steps required for image synthesis.
Model Accessibility and Resources
For researchers and AI enthusiasts, SDXL Turbo’s model weights and code are readily available on platforms like Hugging Face. Additionally, the model’s implementation can be found in Stability AI's generative-models GitHub repository, which includes popular diffusion frameworks for both training and inference. These resources are instrumental for anyone looking to explore or utilize this state-of-the-art model in their projects or research.
Interactive Demonstrations and Tutorials
To facilitate understanding and adoption of SDXL Turbo, the website can feature interactive demos and tutorials. These resources can help users experience the model's capabilities firsthand and guide them through its various applications, from simple text-to-image generation to more complex image-to-image transformations.
Links to Further Reading and Research Papers
Providing direct links to the research paper and other technical documents allows visitors to delve deeper into the science and engineering behind SDXL Turbo. These resources are crucial for academics, researchers, and technology enthusiasts who wish to gain a comprehensive understanding of the model's inner workings.
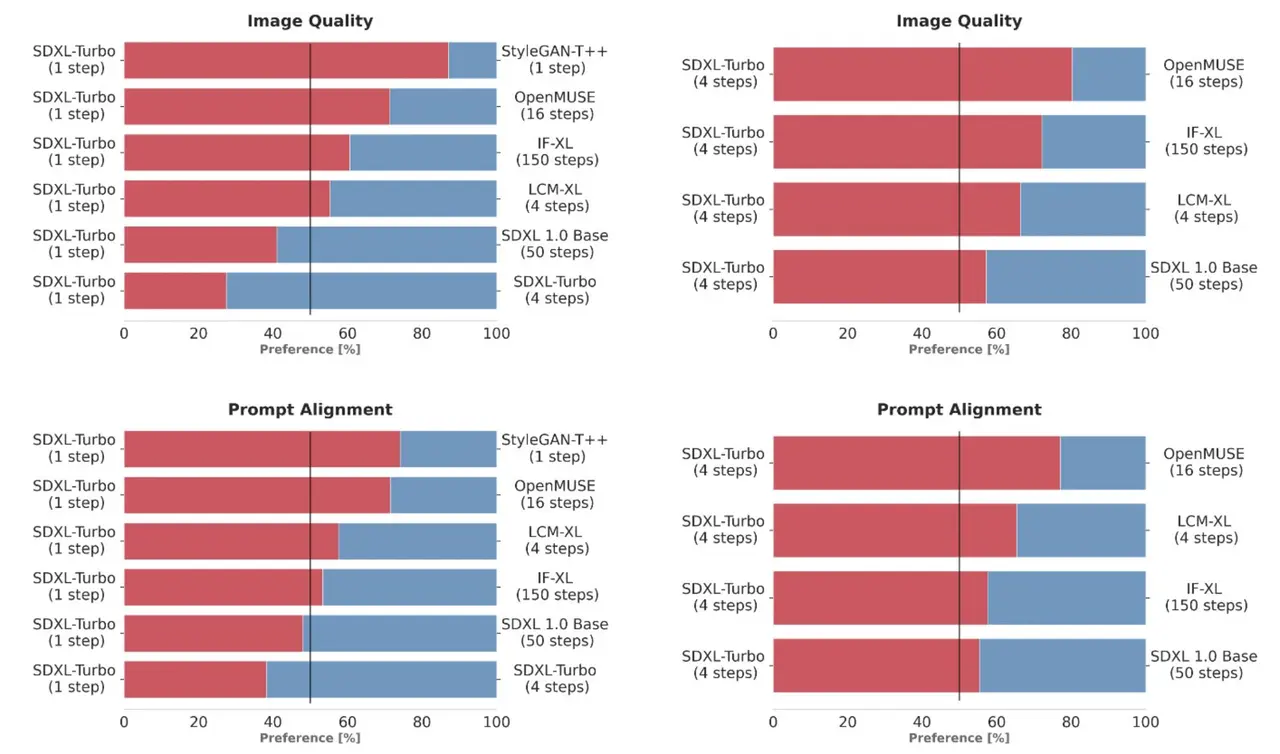
Download, Trial, and Usage Information of SDXL Turbo
Free Trial and Experience on sdxlturbo.ai
The most exciting feature for visitors to sdxlturbo.ai is the opportunity to experience and use SDXL Turbo for free. Emphasize this at the forefront of the section: "Try SDXL Turbo firsthand at no cost on sdxlturbo.ai! Experience the power of real-time text-to-image generation directly through our platform." This invitation allows users to engage with the technology immediately, showcasing the model's capabilities and user-friendliness.
Easy Accessibility for All Users
Highlight the ease with which both novices and experts can access and use SDXL Turbo on the website. The platform is designed to be intuitive, ensuring that even users with minimal technical background can start generating images in moments. This feature broadens the appeal of SDXL Turbo, making it accessible to a wide audience, including educators, artists, researchers, and hobbyists.
Model Download and Implementation
For those interested in more technical engagement, provide clear instructions and links for downloading SDXL Turbo’s model weights and code from repositories like Hugging Face. This section caters to developers and researchers looking to integrate SDXL Turbo into their own projects or conduct in-depth analysis and customization.
SDXL Turbo Related Tweets
Frequently Asked Questions
What is SDXL Turbo?
SDXL Turbo is a state-of-the-art text-to-image generation model that utilizes Adversarial Diffusion Distillation (ADD) for high-quality, real-time image synthesis.
Is SDXL Turbo free to use?
Yes, SDXL Turbo is available for free, non-commercial use on sdxlturbo.ai, where users can experience and test its capabilities.
Can I use SDXL Turbo for commercial purposes?
Currently, SDXL Turbo is released under a non-commercial research license. For commercial use, please contact us through sdxlturbo.ai for further information.
How does SDXL Turbo differ from other text-to-image models?
SDXL Turbo leverages ADD technology, enabling it to generate high-quality images in a single step, significantly faster than traditional multi-step models.
What are the system requirements to use SDXL Turbo?
SDXL Turbo can be used on most modern systems with internet access. For developers, using a system with a capable GPU like NVIDIA's A100 enhances its performance.
Can I integrate SDXL Turbo into my own applications?
Yes, developers can integrate SDXL Turbo into their applications using the model weights and code available on Hugging Face and GitHub, adhering to the non-commercial license terms.
What image resolution does SDXL Turbo support?
SDXL Turbo is optimized for generating 512x512 pixel images, balancing quality and computational efficiency.
Does SDXL Turbo support text-to-video generation?
Currently, SDXL Turbo specializes in text-to-image generation. Text-to-video capabilities are not available in this version.
How can I access SDXL Turbo’s model weights and code?
The model weights and code are available on Hugging Face and Stability AI’s generative-models GitHub repository.
Are there any limitations to the content SDXL Turbo can generate?
Yes, SDXL Turbo may have limitations in rendering legible text, faces, and certain complex scenarios. It’s also governed by an ethical use policy to prevent misuse.
Can SDXL Turbo generate images from any text prompt?
SDXL Turbo is designed to generate images from a wide range of text prompts, though its accuracy and quality may vary depending on the prompt’s specificity and complexity.
Is it possible to customize images generated by SDXL Turbo?
Yes, users can influence the outcome by adjusting the text prompts, though the current version does not support fine-grained control over every aspect of the generated image.
How does SDXL Turbo ensure the ethical use of AI?
SDXL Turbo adheres to Stability AI’s Acceptable Use Policy, which guides against generating harmful or misleading content.
What support is available for new users of SDXL Turbo?
New users can access a range of resources, including tutorials, user guides, and a community forum on sdxlturbo.ai.
Can I contribute to the development of SDXL Turbo??
Yes, developers and researchers are welcome to contribute, especially those focusing on AI and image generation technology, by adhering to the guidelines provided on our repository.
Are there any plans to improve SDXL Turbo further?
Continuous improvements and updates are planned, with a focus on enhancing performance, expanding capabilities, and ensuring ethical AI practices.
Can SDXL Turbo be used for educational purposes?
Absolutely, SDXL Turbo is a valuable tool for educational purposes, particularly in fields related to AI, computer graphics, and media studies.
How does SDXL Turbo handle data privacy and security?
User data privacy and security are top priorities. SDXL Turbo complies with all relevant data protection regulations and does not store personal data without consent.
Is there a community for SDXL Turbo users?
Yes, there’s an active online community where users can share experiences, get help, and discuss best practices.
Where can I find more detailed documentation on SDXL Turbo?
Detailed documentation is available on sdxlturbo.ai and within the repositories on Hugging Face and GitHub.